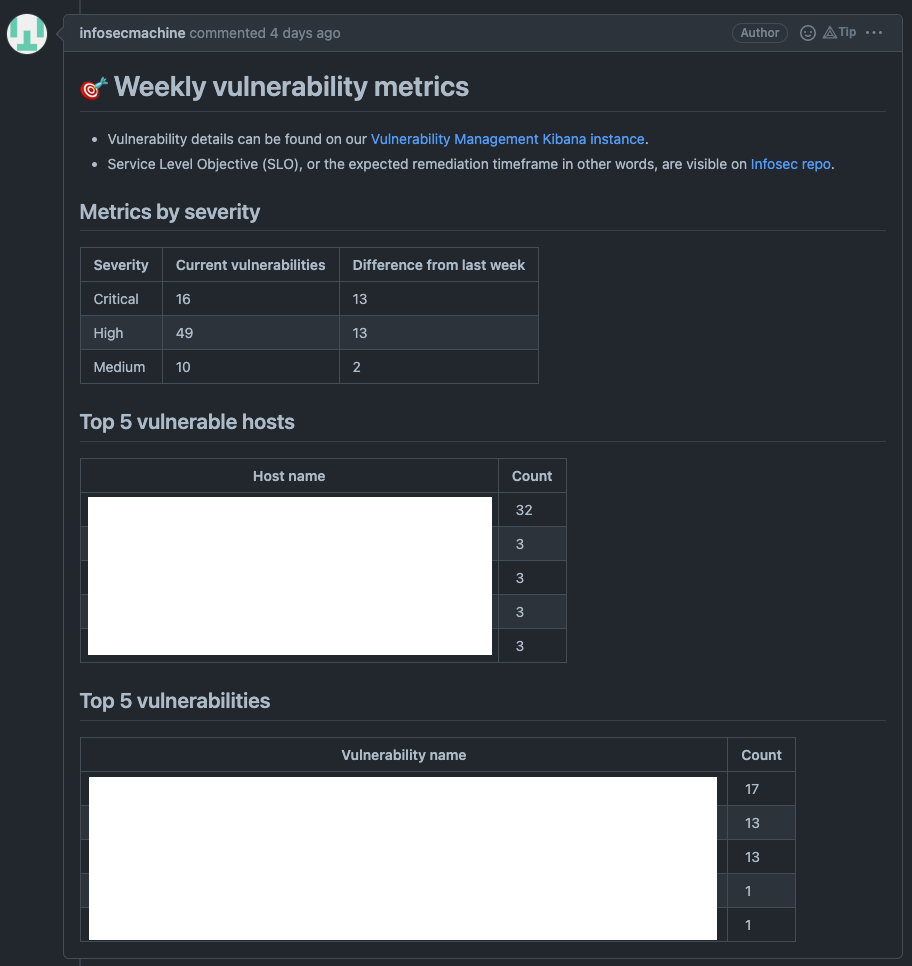
GitHub - HKcyberstark/Vuln_Mod: Vulnerability Assessment Module - OpenVas with Elastic stack using VulnWhisperer

How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog

The Log4j2 Vulnerability: What to know, tools to learn more, and how Elastic can help | Elastic Blog
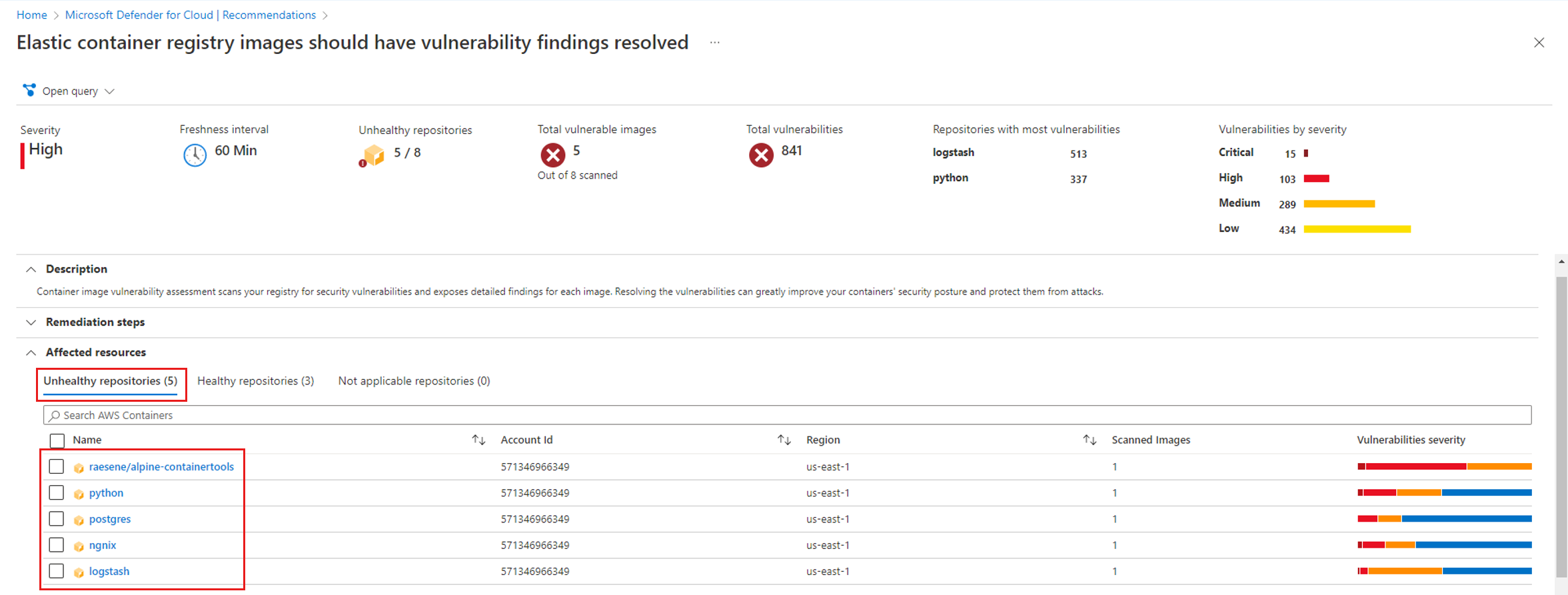
Identify vulnerabilities in Amazon AWS Elastic Container Registry - Microsoft Defender for Cloud | Microsoft Learn

Cisco Patches Elastic Services Controller to Address Critical REST API Vulnerability -- Virtualization Review

Tenable.io Vulnerability Management - subscription license (1 year) - 1 asset - TIOVM-DUPL C - Vulnerability - CDW.com

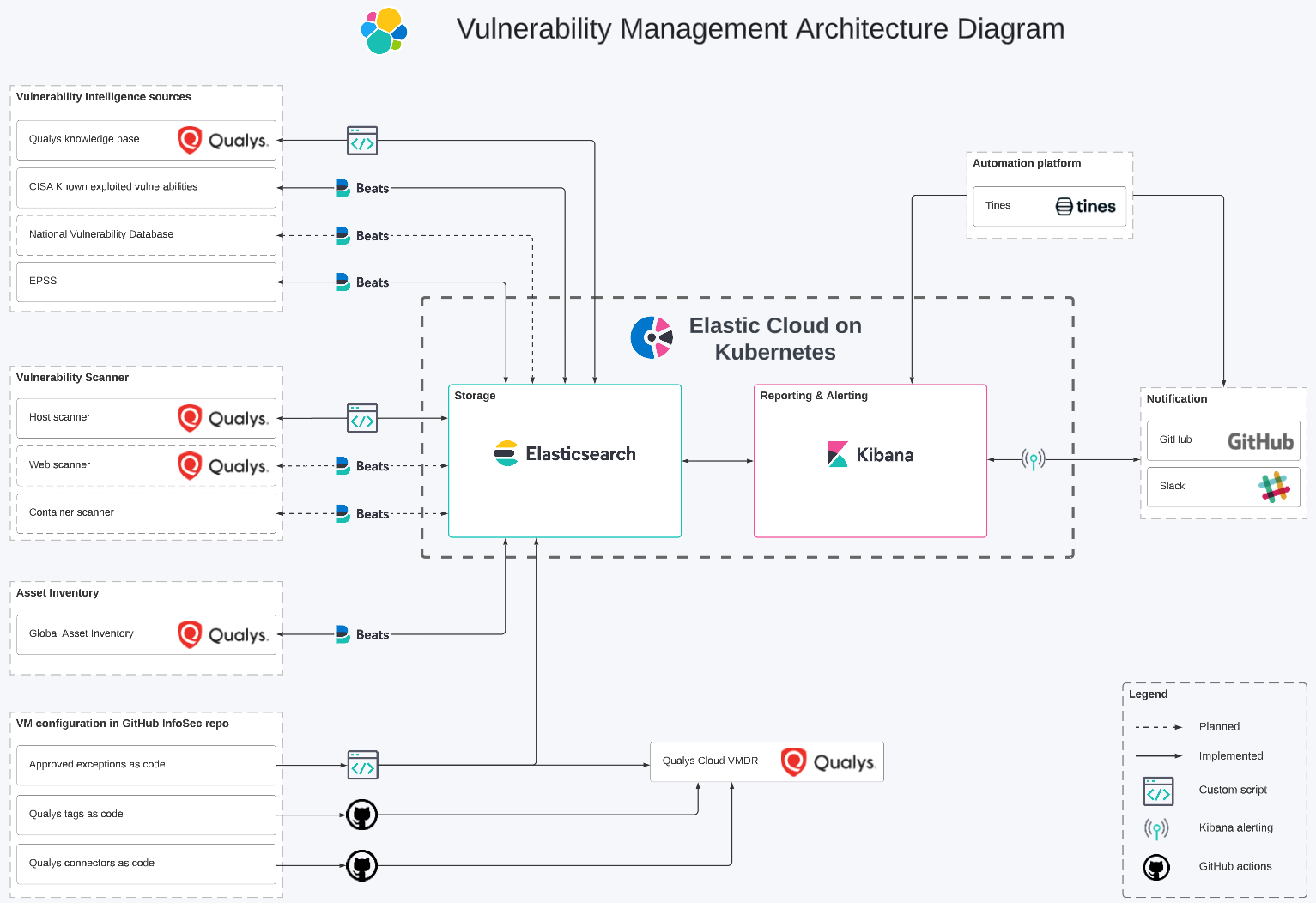
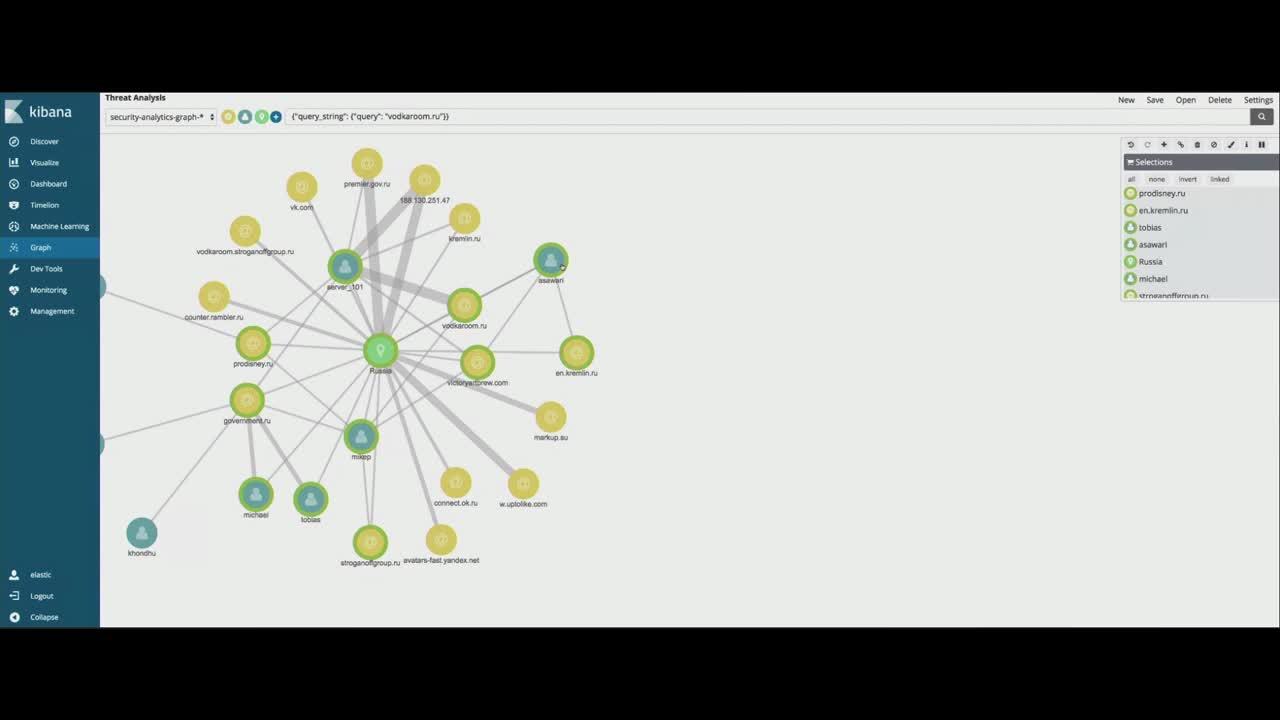



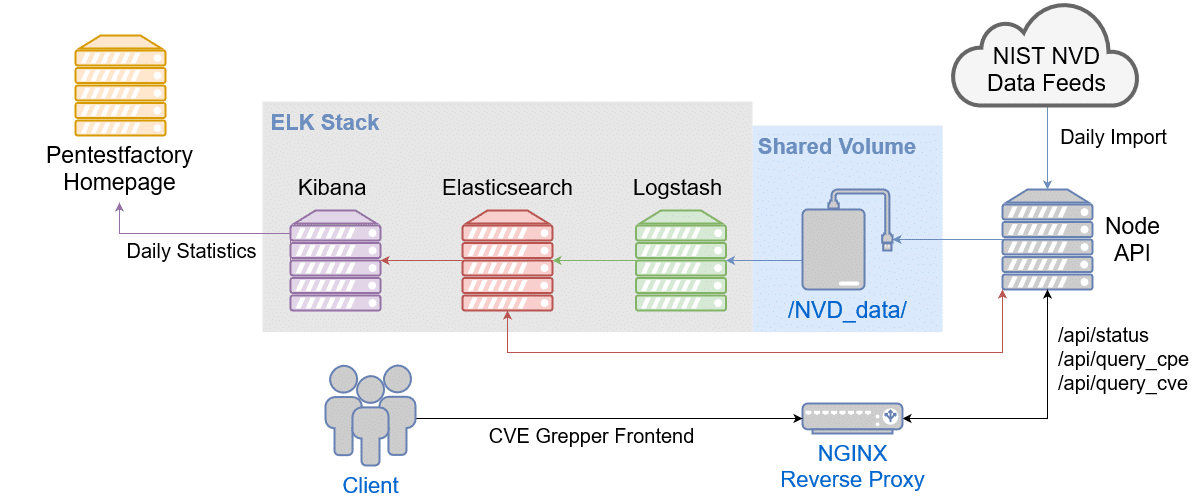

.png)

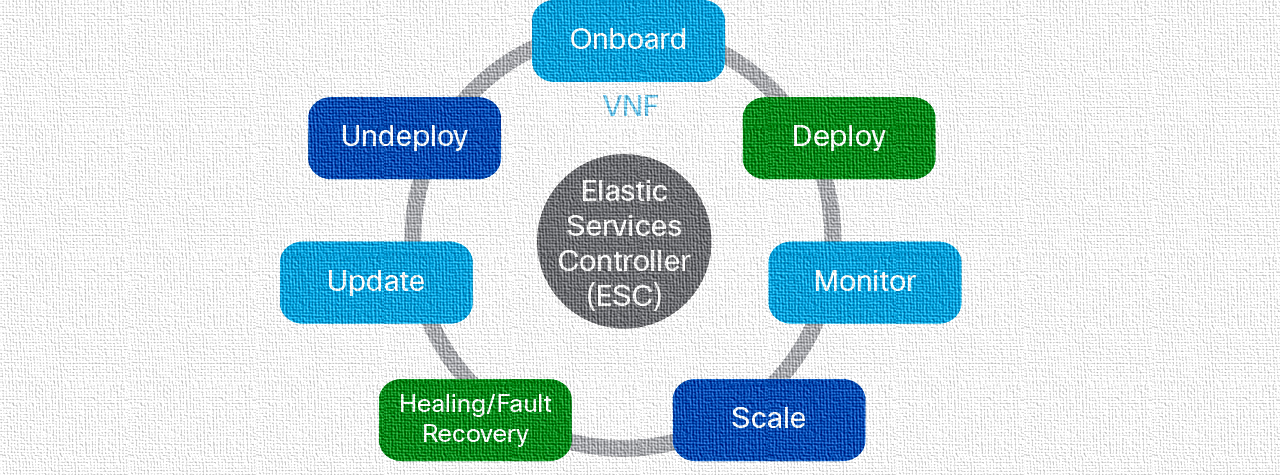
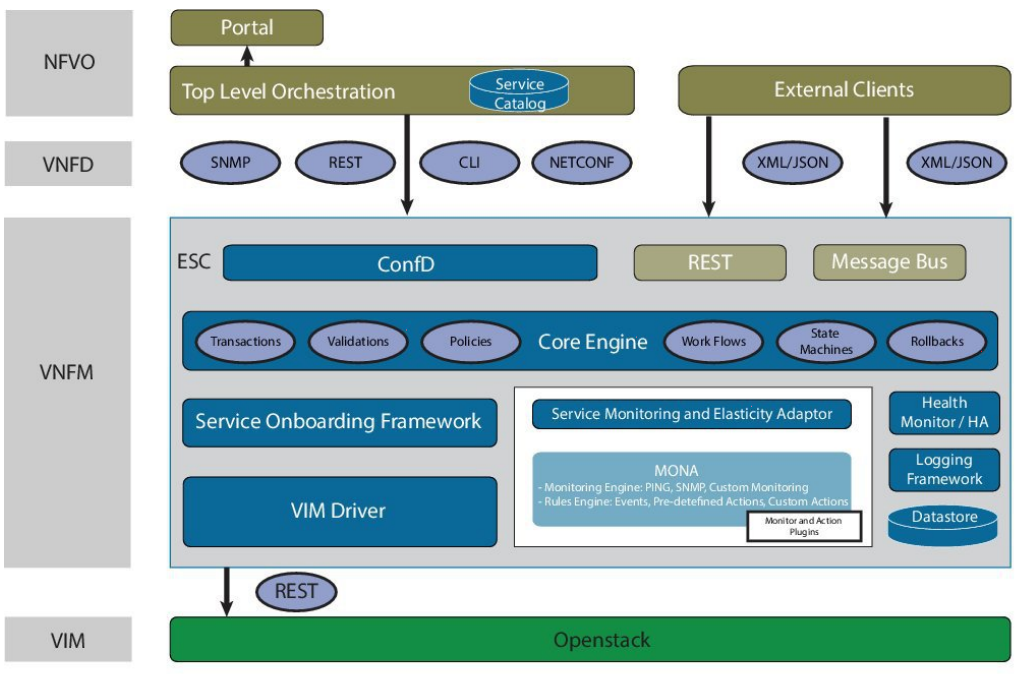

![Cloud Security] [CNVM] Dashboard - Trend graph · Issue #158065 · elastic/kibana · GitHub Cloud Security] [CNVM] Dashboard - Trend graph · Issue #158065 · elastic/kibana · GitHub](https://user-images.githubusercontent.com/51442161/239244621-30f8f709-a05c-4d1f-859c-883d26b20e4b.png)