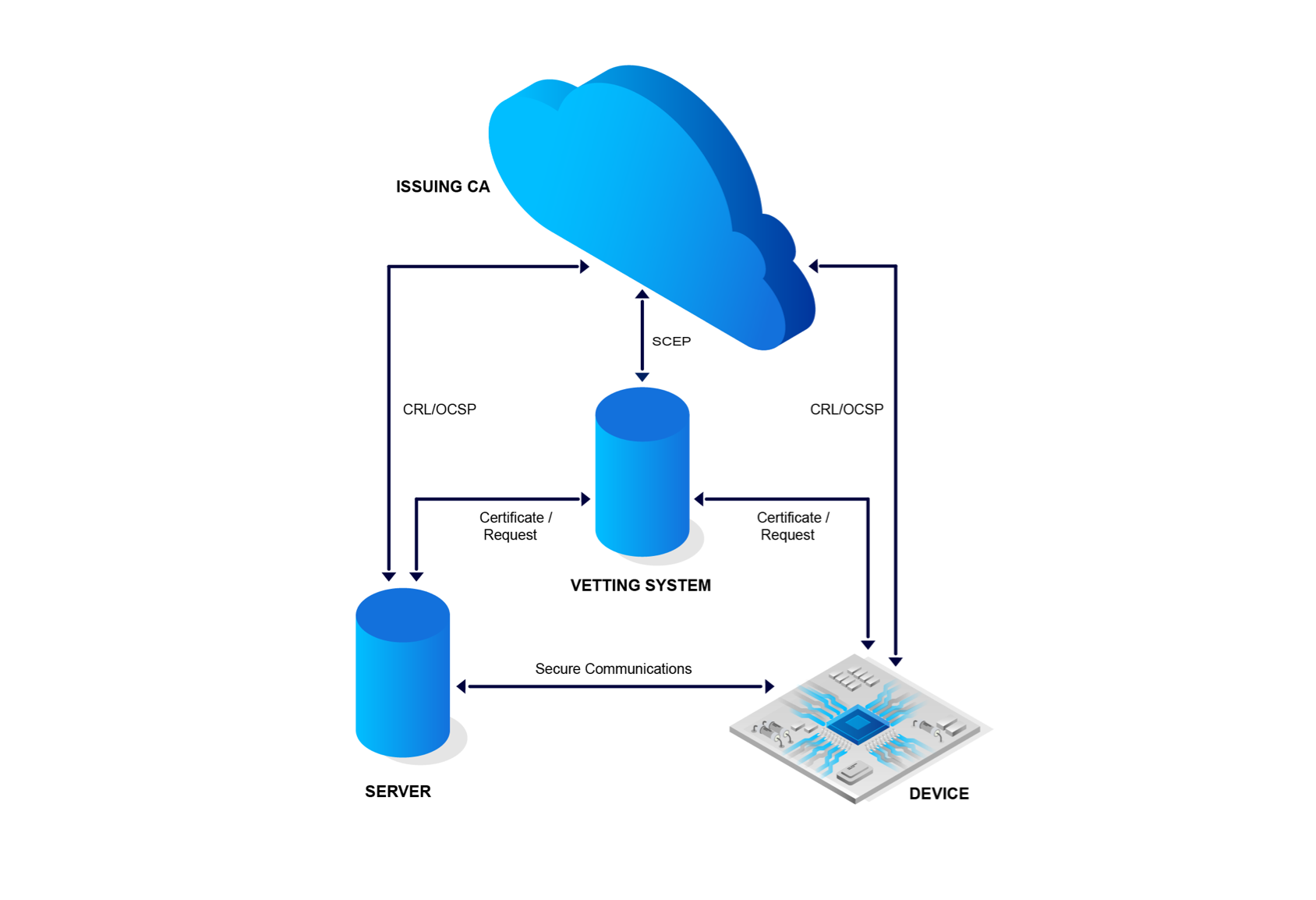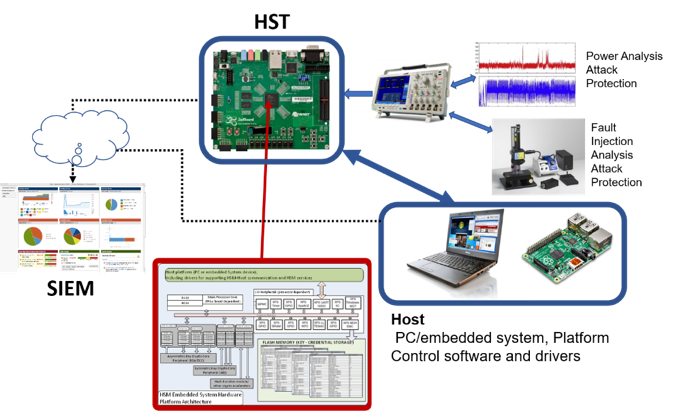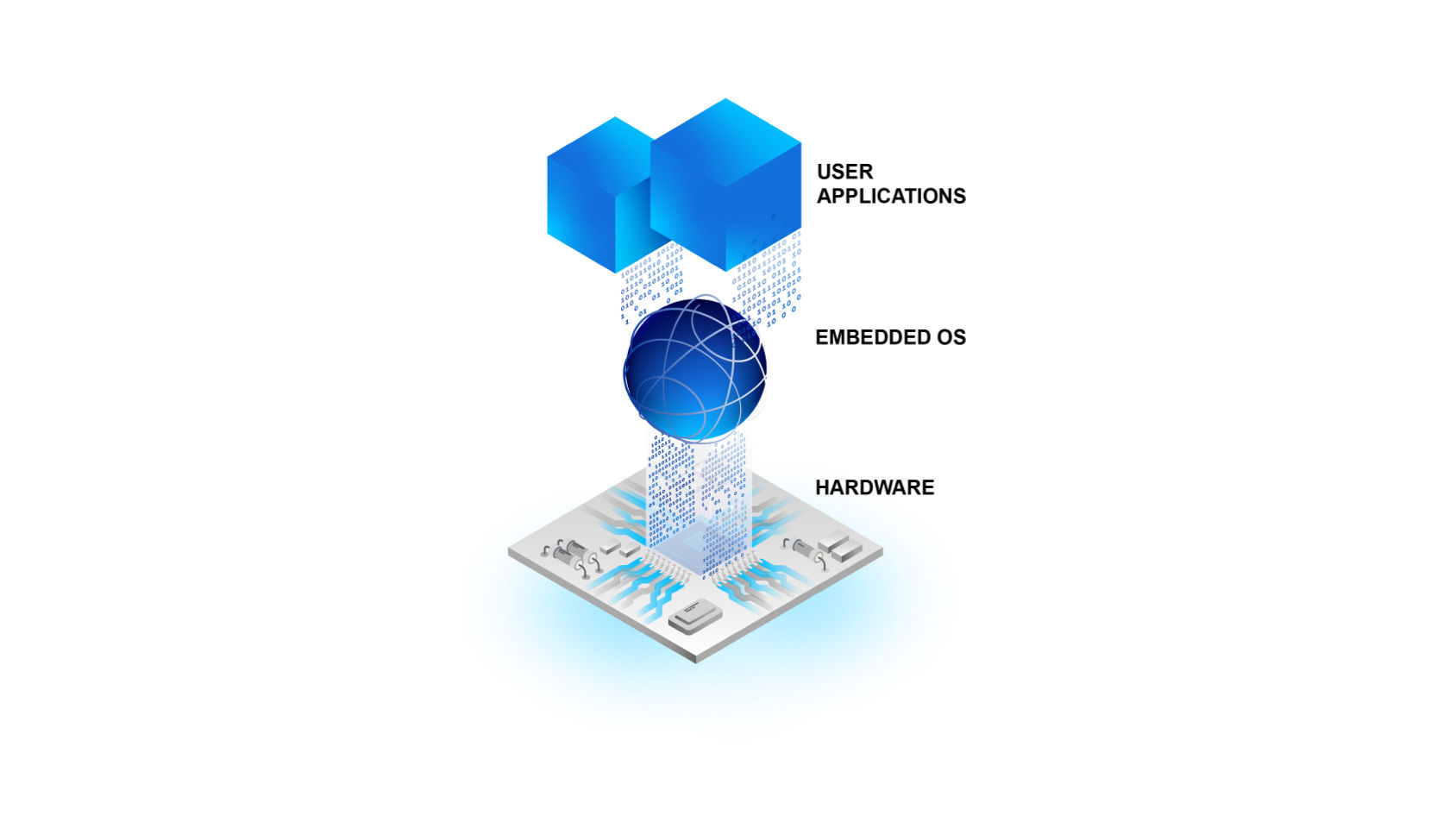
Why low-level code has become the new focal point of cybersecurity for embedded systems - TrustInSoft, exhaustive static analysis tools for software security and safety
Why low-level code has become the new focal point of cybersecurity for embedded systems - TrustInSoft, exhaustive static analysis tools for software security and safety



![Development of Secure Embedded Systems Specialization [4 course series] (EIT Digital) | Coursera Development of Secure Embedded Systems Specialization [4 course series] (EIT Digital) | Coursera](https://s3.amazonaws.com/coursera_assets/meta_images/generated/XDP/XDP~SPECIALIZATION!~embedded-systems-security/XDP~SPECIALIZATION!~embedded-systems-security.jpeg)