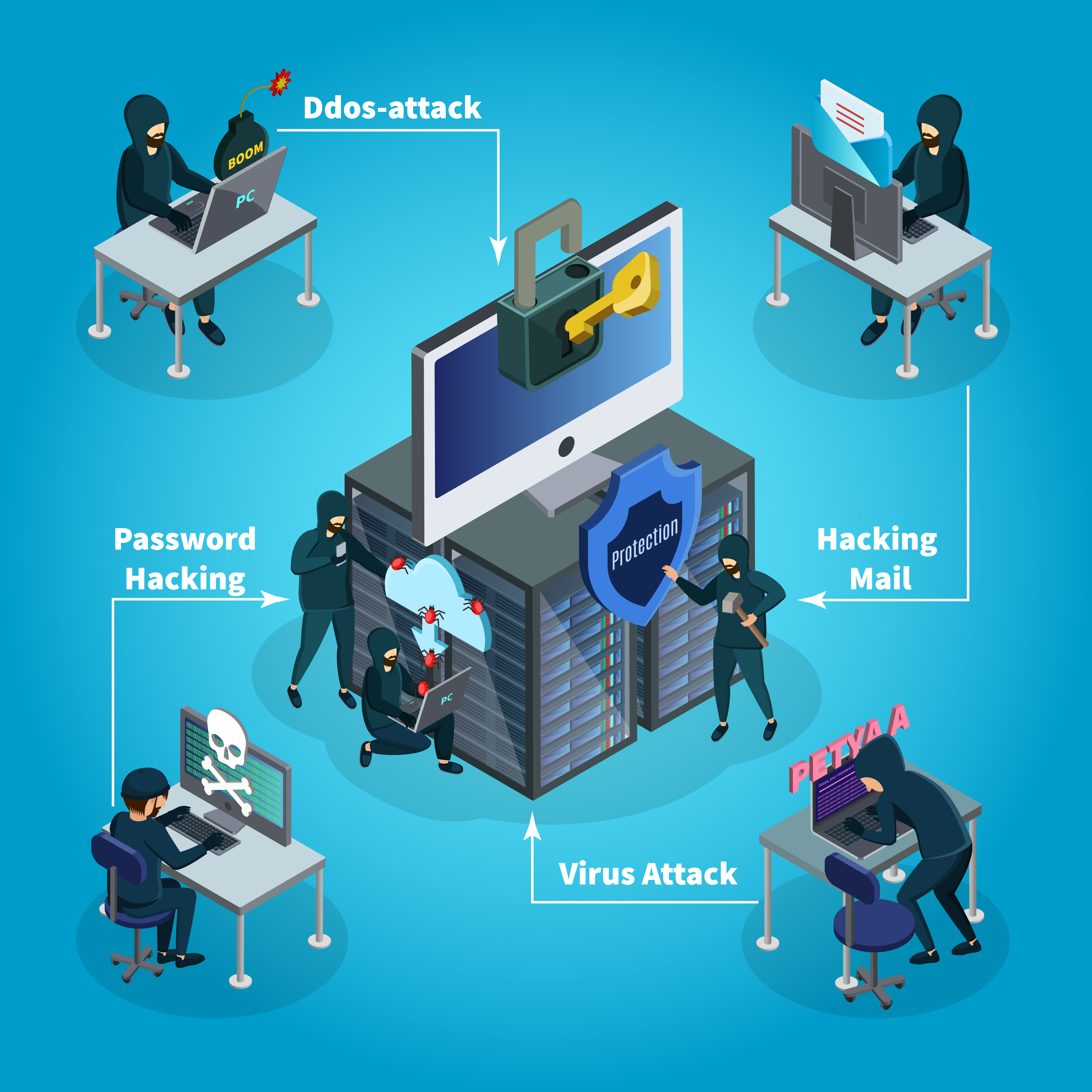
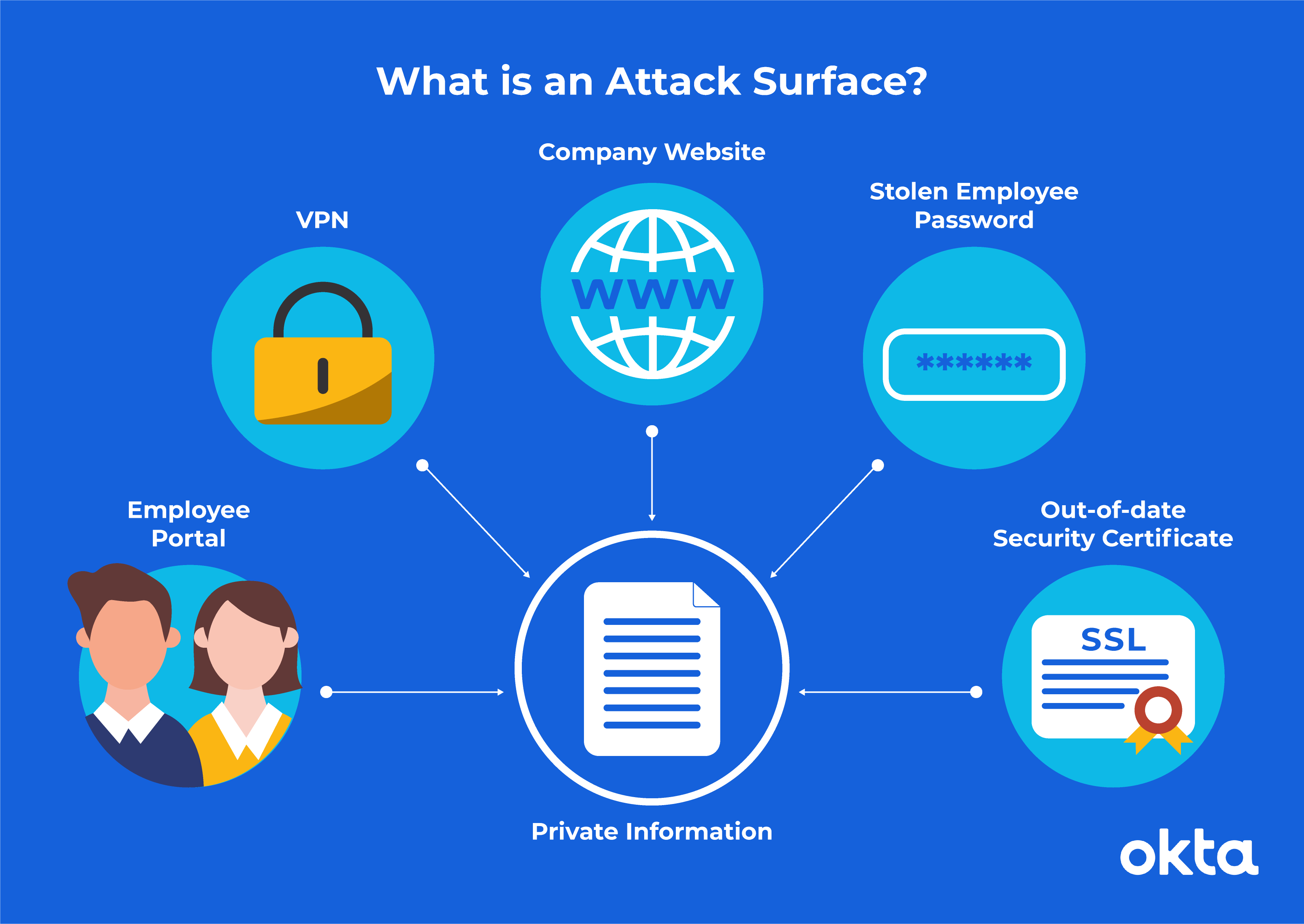
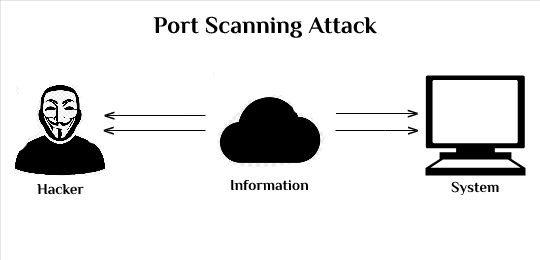
What are different types of attacks on a system – Infosavvy Cyber Security & IT Management Trainings

Ransomware attack hits Goa's flood monitoring system; demand crypto as payment | Latest News India - Hindustan Times

It could be taken down by an enthusiastic child': Whitehall wide open to cyber-attack, warn campaigners | Cybercrime | The Guardian

FBI warns healthcare systems of Hive ransomware following Memorial Health System attack | Fierce Healthcare